University of Science and Technology Yemen
The best private university
The University of Science and Technology seeks to provide outstanding educational, research and consultancy services at the local, regional and international levels with a commitment to social responsibility through qualified staff, advanced curricula, and an equipped environment that stimulates creativity, and effective partnerships, all of which contributes to the production of efficient outputs that meet the needs of the labor market and other developmental requirements, in accordance with academic quality and accreditation standards.

Faculties & Underlying Programmes In UST Yemen
A wide range of programmes & specialties in both undergraduate and postgraduate studies.
Research & Publication by UST Yemen
The scientific journals issued by the University of Science and Technology have obtained advanced ranks in the classification of the impact factor of the refereed Arab scientific journals 2020, issued by the annual report of the Association of Arab Universities on the refereed scientific journals.

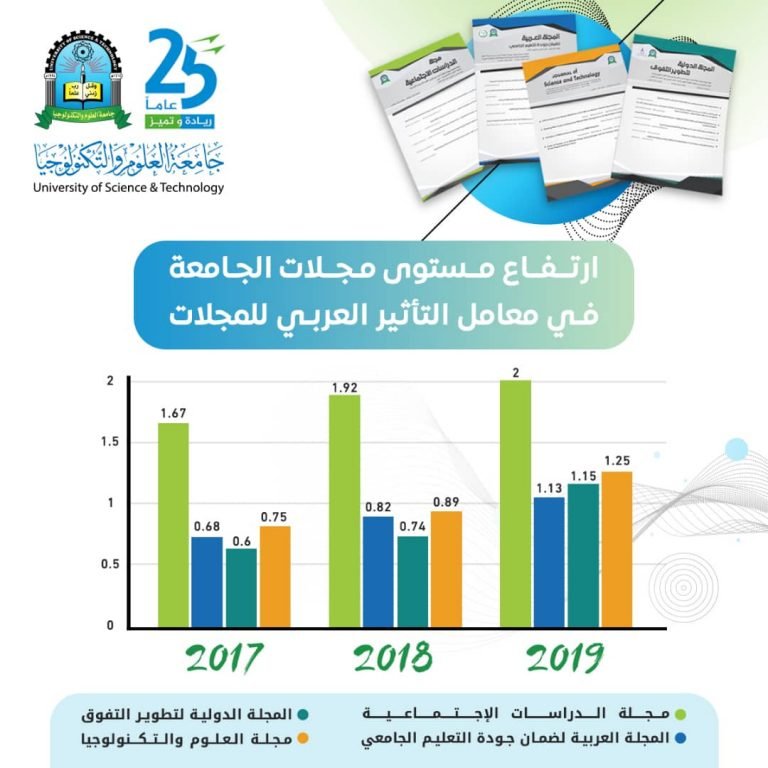
Journals of University of Science and Technology in Yemen
UST Journals
News About University of Science and Technology in Yemen

اختتام برنامج تهيئة أعضاء هيئة التدريس الجدد 2025–2026
اختتمت عمادة التطوير وضمان الجودة بجامعة العلوم والتكنولوجيا – المركز الرئيس عدن، اليوم الأحد 5 أكتوبر 2025م، برنامج تهيئة أعضاء

الماجستير بامتياز للباحثة نسيبة سقاف محمد علوي
منحت عمادة الدراسات العليا والبحث العلمي بجامعة العلوم والتكنولوجيا – المركز الرئيس عدن درجة الماجستير بتقدير امتياز في إدارة الأعمال

تدشين الدراسة في برنامج ماجستير علوم طب الأسنان للعام الجامعي 2025–2026
تدشين الدراسة في برنامج ماجستير علوم طب الأسنان للعام الجامعي 2025–2026 دشنت عمادة الدراسات العليا والبحث العلمي بجامعة العلوم والتكنولوجيا

الماجستير بامتياز للباحث نصر ناجي عباس ناجي
منحت عمادة الدراسات العليا والبحث العلمي بجامعة العلوم والتكنولوجيا – المركز الرئيس عدن درجة الماجستير بتقدير امتياز في إدارة الأعمال
International Partners of the University of Science and Technology in Yemen















































STRATEGIC PLAN OF THE UNIVERSITY of Science Technology Yemen
A participatory and transparent management understanding, the effective and efficient use of resources, performance-based assessment and budgeting as well as the rapid developments experienced in technology and communication methods have enabled The University of Science and Technology to act on its strategic plans that have led to fundamental transformations in the last few years.
Within its framework of embracing an ambitious and long-term strategic plan, the University of Science and Technology, USTY applied the Balanced Scorecard (BSC) approach. Beginning with identifying the strategic goals as per the four dimensions of the BSC, many sub-goals have been branched off from the four strategic goals. Each sub-goal is achieved through the implementation of projects to achieve the goal directly. Indicators were developed to measure the achievement of the sub-goals. The follow-up and assessment mechanism is regularly and continuously implemented according to the BSC instruments prepared previously for this purpose. Through a system of monthly and quarterly reporting from all departments and branches of the University in Yemen, we developed criteria for measuring the implementation and success of the projects on time. Any shortfalls are rectified through corrective action plans.
In order to establish its mission of becoming a leading institute both locally and internationally, USTY has set strategic goals and measurable targets, measuring its performance in line with predetermined indicators and monitor and evaluating the implementation within the framework of development plans, programs.
The University of Science and Technology is now the leading institute in Yemen, offering a total of 45 undergraduate, postgraduate and distance learning programmes in all fields. Equipped with advanced learning facilities, USTY has also been able to run 7 developmental and consultation centres to serve students with aligning interests. The university’s research publication work is also well-established, with 5 journals in the fields of medicine, quality assurance, science and technology, talent development and other fields.
University Blog

In a joyful festive atmosphere, the University of Science and Technology - Aden celebrates its thirtieth anniversary
Aug 14, 24In a joyful festive atmosphere: University of Science and Technology - Aden celebrates its thirtieth anniversary With a magnificent official and academic presence, the University of Science and Technology - Aden, which is considered the best university in Yemen and one of the most prominent…

Medical Camps – Entitlement to Health Care for All
Apr 30, 24Medical Camps - Entitlement to Health Care for All Medical camps occupy an important place in the humanitarian work system, as they provide their services to needy groups in society, or those who suffer from a lack of services…

E-learning: Prospects, Challenges, and a Pioneering Experience for the University of Science and Technology
Apr 30, 24E-learning: Prospects, Challenges, and a Pioneering Experience for the University of Science and Technology E-learning has gained great importance due to its many advantages that contribute to supporting the educational process and giving it great flexibility. Due to the technological development…

E-Learning at the University of Science and Technology: Employing Modern Systems and Applications
Jan 10, 24E-learning at the University of Science and Technology: Employing modern systems and electronic applications For more than a quarter of a century, the University of Science and Technology has proven its leadership in the field of adopting and developing e-learning and distance learning…

Leadership of the University of Science and Technology in the field of sustainable development and development
Jan 10, 24Pioneering the University of Science and Technology in the field of sustainable development and development In the world of higher education and scientific research, the University of Science and Technology (UST) stands out as a beacon of sustainable development and development. With its commitment to fostering an environment that contributes significantly to…

University of Science and Technology, Women's Gateway to Academic and Professional Excellence
Jan 10, 24University of Science and Technology - Main Center Aden: Women’s Gateway to Academic and Professional Excellence In a world accelerating the pace of scientific and technological progress, the University of Science and Technology stands out as a model to be emulated in the field of education…

International Cooperation Programs - University of Science and Technology - Headquarters - Aden
Mar 07, 23International Cooperation Programs - University of Science and Technology - Headquarters - Aden Based on the university’s quest, and since its first experiences, to obtain the highest levels of local and international academic accreditation, and to ensure that its scientific outputs match…

Field Training University of Science and Technology - Headquarters - Aden
Mar 07, 23Field Training - University of Science and Technology - Headquarters - Aden Out of the university's keenness to rehabilitate its students and provide them with skills and experience, link between theoretical knowledge and practical application, and provide students with the opportunity to discover…

Community service at the University of Science and Technology
Feb 14, 23Community Service at the University of Science and Technology Introduction: Community service occupies an important place in our contemporary world. As it has become an urgent responsibility that falls on the shoulders of various organizations, whether they have…










